
You Could Be the Next Target
Hello friend,
Recently, Francesco Ciulla got hacked. His X account and I believe Instagram and Github accounts, got stollen. Truth be told, we tend to neglect the importance of security until it’s too late.
Talking to more close friends, I realized that they often neglect the importance of security and privacy when speaking about digital world. Don’t get me wrong, I did the same. There are many, many threats out there. Hackers, or rather, scammers have gotten very creative, and they have different reasons why they might target you. Just to name a few: money theft, identity theft, taking control over your computer or infrastructure for further attacks, benefitting from your follower base, and more.
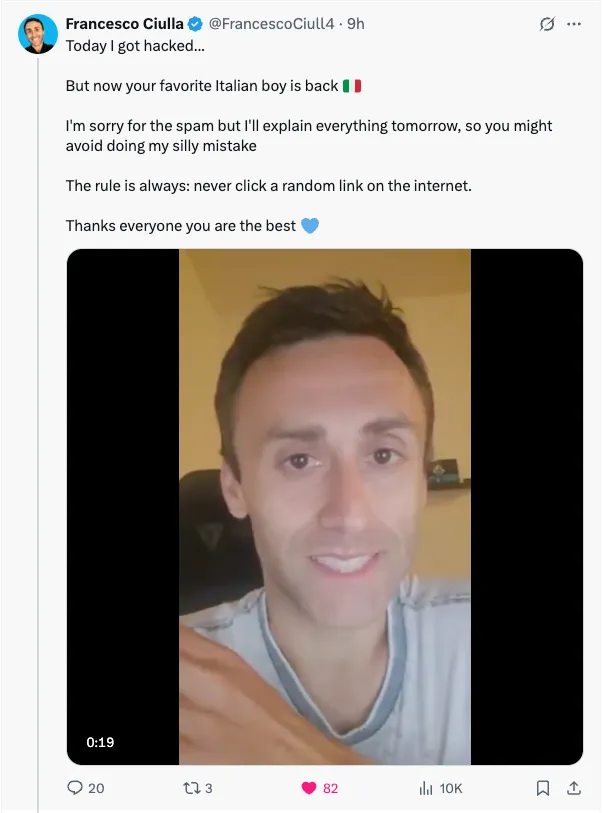 Source: https://x.com/FrancescoCiull4/status/1923167743508926974
Source: https://x.com/FrancescoCiull4/status/1923167743508926974
I have to say I’m not an expert when speaking of cyber security. I’ve tried to learn some best practices on how to protect myself. I’m writing this post not from a professional or expert standpoint, but rather to let you know what I do, hoping that this is helpful to you in preventing future attacks.
Before diving into the lists, there’s one more idea I have to mention: there’s no 100% secure system. If someone says that their software is 100% hack-proof, they’re lying. There’s no such thing.
Also, using a super secure product doesn’t mean we’re not vulnerable. Social media platforms, for example, have different security mechanisms in place. In a sense, we can call them secure. But most of the time, we as humans are the weak link in the chain. Our own errors and careless habits often make us easy targets.
We the weak link in the chain. Our own errors and careless habits often make us easy targets.
I’ve prepared a list of quick tips, in no particular order or priority:
1. “Never click a random link on the internet”
I’m starting the list with Francesco’s advice: don’t click links on the internet. We tend to receive many links on either social media platforms, WhatsApp or email. Don’t click them. Verify if the sender is actually who they claim to be.
As an example, I’ll share with you a screenshot of a message I got in an Instagram chat (check the screenshot below).
I’ve already talked about this in a past Instagram reel. I keep receiving these messages pretending to be from Facebook. They are not. They are scammers. Don’t click those links. Even though the message might we well formulated and formatted, you should always be a bit skeptical.
One way you could verify the validity of a link is by checking the domain.
This is the link to my Instagram profile: https://www.instagram.com/razvanmuntian
If you look closely, the domain is instagram.com, and the page or account starts from / onwards (/razvanmuntian). So you can easily identify that a URL is an Instagram profile if the link starts with instagram.com or www.instagram.com.
In the image below, the scammers ask me to verify my identity and click the link that starts with repair.expense-management-core.eu. Facebook and Meta does not own that domain. That’s not the real Facebook or Instagram link.
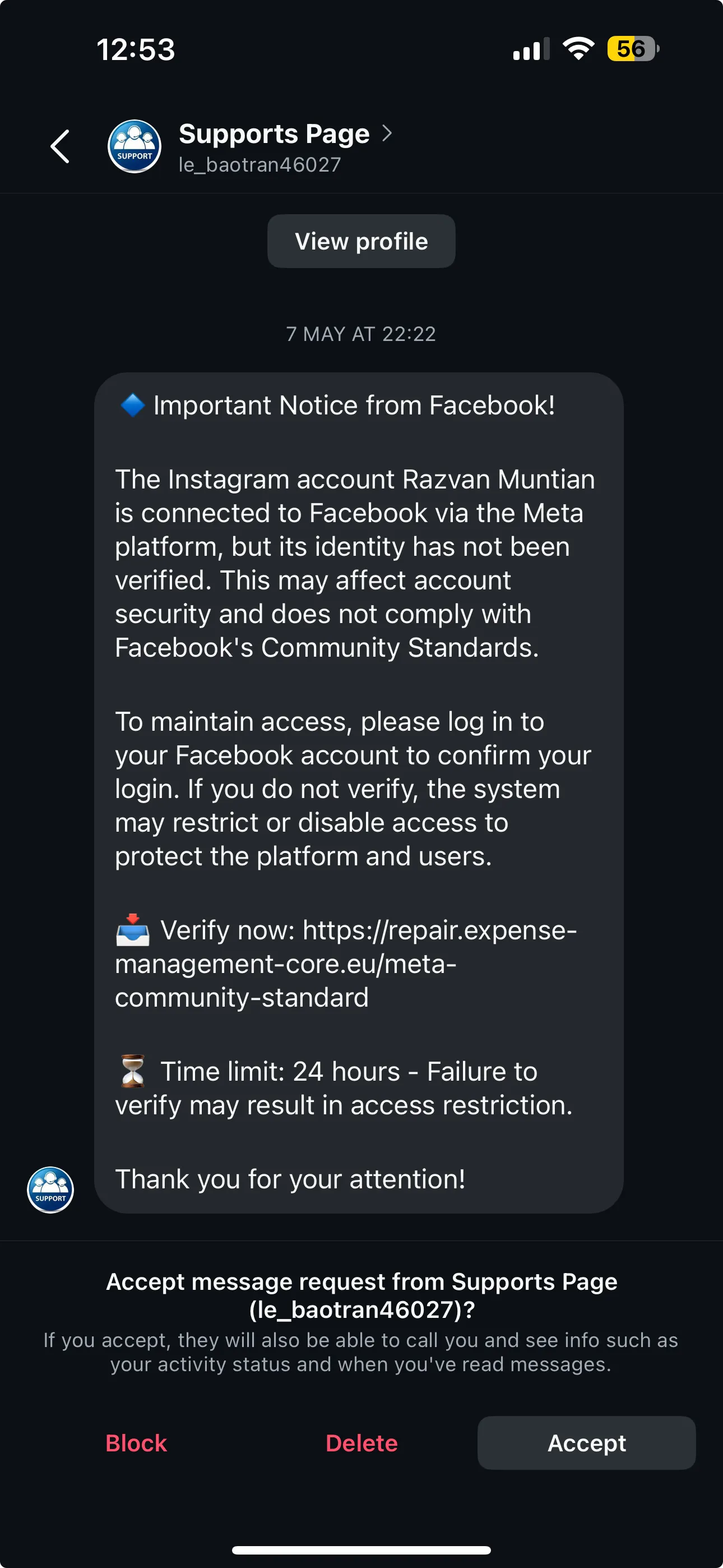
2. Temporary email address
Most of the online services ask for your email address. You provide your email address to Facebook, to an e-commerce platform, to your banking or to Youtube.
But what if you want to download a free e-book or digital product from a webpage, but they ask you for your email address? Some pages might look sketchy, but others look profession and legit.
What might happen is your email ends up in a list with tens or hundreds of thousands of other emails that are sold online on the black market. And you end up receiving many spam emails with fake links that you’re tempted to click. If you click them you end up infected and so on.
What can you do to prevent this from happening? There’s a service I use that I believe is great for this use case: mail.tm
You can create free disposable email addresses. Addresses will be wiped out every once in a while. Don’t use them for anything permanent, but rather for temporary purposes. That’s a great way to ensure your real email address stays safe.
3. Password manager
We tend to have weak passwords, and to use the same weak passwords across all platforms. What happens if someone manages to steal your password, or if one website is vulnerable and the database of that particular app gets stolen?
This might sound crazy, but it happens quite frequently. Don’t underestimate this. Hackers target various vulnerabilities and platforms to steal whatever they can.
A common misconception is that no one will target you because you’re too small and there’s no point. You might be right: no one would directly target you. But there are scripts (viruses, as everyone calls them) that run automatically. You might just be a collateral victim.
How to prevent this? Use complex, unique passwords.
What’s the easiest way to do this? Use a password manager.
I personally use https://bitwarden.com, but you can do your own research. Ideally, you’d use a randomly generated password that contains letters, numbers, and symbols. If you use words, there are dictionaries that make it easier to crack your password in milliseconds (the technique is called brute force).
4. Create a recovery email
Maybe you never thought about this: you could create an email address whose main purpose is recovery. You don’t want to lose access to your main email address. Don’t use the recovery email to log in to websites, to send emails, or for anything other than to recovering your other email address.
Most of the email providers have this option to setup a recovery email. Why not use this feature wisely?
5. Use multiple emails
How many email addresses do you have? I use more than 5 email addresses.
I use one for my personal subscriptions and services, one for social media, more for my business, and others. Why not create more email addresses?
You know that proverb: don’t put all your eggs in one basket. That’s what we try to do here: mitigate the risk of one email being compromised. If someone breaks into your email and gains access to your banking, social media, Netflix, e-commerce sites, you’ll have a hard time trying to recover and gain control over everything after an attack. Using multiple emails is one way to reduce that risk.
In conclusion
This is not an exhaustive list. I’ll keep writing these small tips now and then, so you can improve your online privacy and security.
I hope I gave you at least a few useful tips and motivated you to do your own research.
See you soon!